 network hacking
Wifi Hacking
Wireless Network Hacking
WEP and WPA-PSK wifi cracking tool
network hacking
Wifi Hacking
Wireless Network Hacking
WEP and WPA-PSK wifi cracking tool
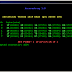
Aircrack-ng (a fork of aircrack) is my main tool for cracking Wi-Fi passwords. It has a wireless network detector, a packet sniffer, WEP a...
A Pakistani Informition Website For Learning and Fun
 network hacking
Wifi Hacking
Wireless Network Hacking
WEP and WPA-PSK wifi cracking tool
network hacking
Wifi Hacking
Wireless Network Hacking
WEP and WPA-PSK wifi cracking tool
Aircrack-ng (a fork of aircrack) is my main tool for cracking Wi-Fi passwords. It has a wireless network detector, a packet sniffer, WEP a...
 network hacking
Wireless Network Hacking
How to disconnect any wifi devices from network
network hacking
Wireless Network Hacking
How to disconnect any wifi devices from network
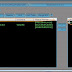
Netcut is mostly used to disconnect any wifi device from network and Find any IP/Computer/network devices/Phone/Xbox/PSP/PS3/Wii/Ipad anyth...
 network hacking
Wireless Network Hacking
Wifi hacking Using Backtrack
network hacking
Wireless Network Hacking
Wifi hacking Using Backtrack
Step 1:- First Download Backtrack from the following link: http://www.remote-exploit.org/backtrack_download.html Step 2:- Burn the iso imag...
 network hacking
Telnet command
network hacking
Telnet command
Telnet is a program which runs on TCP/IP. Using it we can connect to the remote computer on particular port. When connected it grabs the dae...
 network hacking
Netstat command
network hacking
Netstat command
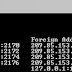
It displays protocol statistics and current TCP/IP network connections. i.e. local address, remote address, port number, etc. It's synta...
 network hacking
Ping Command
network hacking
Ping Command
Ping is part of ICMP (Internet Control Message Protocol) which is used to troubleshoot TCP/IP networks. So, Ping is basically a command that...
 Password cracking
Best Password Cracking Methods
Password cracking
Best Password Cracking Methods
Top Ten Password Cracking Methods 1. Dictionary attack "This uses a simple file containing words that can, surprise surprise, be found ...
 Important Tricks
Windows Event Viewer Most important Trick
Important Tricks
Windows Event Viewer Most important Trick
Do you want to know whether your PC was used in your absence? Just follow these simple steps: 1:Goto Run and type eventvwr.msc in the Run di...
Advanced ID Creator: Advanced ID Creator skilled is a simple to use nonetheless powerful software system resolution developed to assist you ...
Here is mostly top keyloggers.!!! 1:REFOG Free Keylogger: Who Is It For? Concerned parents all over the world use Refog Free Keyl...